Content Court are cool people. Even when they're taking somebody like the Quartering down, it's an eye sore of listen to Q's voice. The overly self smugness and satisfaction wreaks of him. Thank you for the video thoughNot really a new event but this video is so good
Funny events in anti-woke world
- Thread starter Agema
- Start date
Remember what happened when he finally got around to telling people to get the vaccine in one of his rallies? His followers booed him. (And then he went right back to murmuring "it's your choice, it's your choice".) The ringmaster lost control of the circus.Didn't it take some time for Trump to admit he was vacinated? Probably because he feared losing votes from it.
No, I don't. Nicky want's to be a fucking idiot, let her.Yet it's not me you have to convince it's Nicki Minaj you have to convince that her family member is lying or wrong
I repeat; leftists acting like dipshits still doesn't make the right wing correct.Never said it did make the correct but shouldn't you be a little concerned about people acting at least as bad as if now worse than them?
He also pushed the hydroxychloroquine hype train. Forgot that?I mean you can't even blame Trump as he's very much on record as being pro vaccine lol
Thank you for reminding me of that.And that's acting to ignore Trump being on record saying he downplayed the thing deliberately to try and prevent panic and mass panic buying
You know what we in the adult world call waht he did? It's called a LIE.
Well now you have the problem of idiots still being idiots don't you?No, I don't. Nicky want's to be a fucking idiot, let her.
And two wrong still will not make a right. You'd think the party / side claiming to be better would want to I dunno try to live up to that ideal a bit more?I repeat; leftists acting like dipshits still doesn't make the right wing correct.
Which at the time was being looked into as a possible treatment (in before people bring up the Brazilian study showing it doesn't work where the Doctors were found to be giving patient 10 times or more the recommended doses). Trump probably got briefed on it by medical advisers and said about it because Trump wanted to try and give people hope or something. Oh and half the controversy around it started because a life long democrat voter claimed she'd given it to her husband and herself because she heard Trump say about it on the news.......... A life long Democrat voter with a social media history of saying how Trump couldn't be trusted and court convictions for domestic violence against partner previously and somehow her husband died of the fish tank cleaner poisoning while she survived well enough that within a week or less she was selling her story to the press........He also pushed the hydroxychloroquine hype train. Forgot that?
It's also called how Politicians have to act sometimesThank you for reminding me of that.
You know what we in the adult world call waht he did? It's called a LIE.
This just in, GOP mad that the Progressive Dems strip funding for the Iron Dome from a bill that the GOP was going to vote against anyway
A lot of other nations downplayed the potential severity too or put on a show of how they had it well under control so people shouldn't worry. The reason people look at Trump and the narrative being what it is, is simply people wanted to hate Trump and so were obstinately against him. I mean there were Democrat Mayors etc at the start on about how it was perfectly safe and to come join street festivals etc and no masks needed because it was perfectly safe and only racists were whipping up fear of some silly virus because it was from China.Which is absurd and self defeating. Even if we take Trump on his word on that one it still means he deliberately downplayed a dangerous virus for dubious reasons. The rest of the world didn't fly into a blind panic on hearing Covid existed. But you know what might create a panic? If there's a dangerous pandemic that everyone knows is dangerous except for the government which claims its not dangerous which in turn means they won't take steps to handle it. What also might create panic is if the citizenry are told time and again covid isn't a big deal and thus aren't careful which leads to vovid numbers spiking and giving everyone really good reasons to panic.
Even if we bizarrely enough believe Trump was acting in good faith then the entire affair still shows he's completely incompetent and should never have been given power to begin with. But its more likely that Trump was not acting in good faith and that his actions can be explained by the demagogic toolbox just not being suited for covid
I think the WHO has done enough undermining itself for a good decade or so at this point it didn't need Trump to help.Didn't it take some time for Trump to admit he was vacinated? Probably because he feared losing votes from it. But yeah, Trump is at least not vocally anti vax per se. But his constant demonization and undermining of any expert, virologist or doctor is a big part of the reason why people are so zealously against vaccines.
Bloody paywall, "democracy dies in the dark" except if that darkness is a paywall, eh? Anyway, surprised to see anonymous do something of political worth for once.Epik long has been the favorite Internet company of the far-right, providing domain services to QAnon theorists, Proud Boys and other instigators of the Jan. 6 attack on the U.S. Capitol — allowing them to broadcast hateful messages from behind a veil of anonymity.
But that veil abruptly vanished last week when a huge breach by the hacker group Anonymous dumped into public view more than 150 gigabytes of previously private data — including user names, passwords and other identifying information of Epik’s customers.
Extremism researchers and political opponents have treated the leak as a Rosetta Stone to the far-right, helping them to decode who has been doing what with whom over several years. Initial revelations have spilled out steadily across Twitter since news of the hack broke last week, often under the hashtag #epikfail, but those studying the material say they will need months and perhaps years to dig through all of it.
“It’s massive. It may be the biggest domain-style leak I’ve seen and, as an extremism researcher, it’s certainly the most interesting,” said Megan Squire, a computer science professor at Elon University who studies right-wing extremism. “It’s an embarrassment of riches — stress on the embarrassment.”
Epik, based in the Seattle suburb of Sammamish, has made its name in the Internet world by providing critical Web services to sites that have run afoul of other companies’ policies against hate speech, misinformation and advocating violence. Its client list is a roll-call of sites known for permitting extreme posts and that have been rejected by other companies for their failure to moderate what their users post.
Online records show those sites have included 8chan, which was dropped by its providers after hosting the manifesto of a gunman who killed 51 Muslims in Christchurch, New Zealand, in 2019; Gab, which was dropped for hosting the antisemitic rants of a gunman who killed 11 people in a Pittsburgh synagogue in 2018; and Parler, which was dropped due to lax moderation related to the Jan. 6 Capitol attack.
Epik also provides services to a network of sites devoted to extremist QAnon conspiracy theories. Epik briefly hosted the neo-Nazi site Daily Stormer in 2019 after acquiring a cybersecurity company that had provided it with hosting services, but Epik soon canceled that contract, according to news reports. Epik also stopped supporting 8chan after a short period of time, the company has said.
Earlier this month, Epik also briefly provided service to the antiabortion group Texas Right to Life, whose website, ProLifeWhistleblower.com, was removed by the hosting service GoDaddy because it solicited accusations about which medical providers might be violating a state abortion ban.
An Epik attorney said the company stopped working with the site because it violated company rules against collecting people’s private information. Online records show Epik was still the site’s domain registrar as of last week, though the digital tip line is no longer available, and the site now redirects to the group’s homepage.
Epik founder Robert Monster’s willingness to provide technical support to online sanctuaries of the far-right have made him a regular target of anti-extremism advocates, who criticized him for using Epik’s tools to republish the Christchurch gunman’s manifesto and live-streamed video the killer had made of the slaughter.
Monster also used the moment as a marketing opportunity, saying the files were now “effectively uncensorable,” according to screenshots of his tweets and Gab posts from the time. Monster also urged Epik employees to watch the video, which he said would convince them it was faked, Bloomberg News reported.
Monster has defended his work as critical to keeping the Internet uncensored and free, aligning himself with conservative critics who argue that leading technology companies such as Facebook, Twitter, Amazon and YouTube have gone too far in policing content they deem inappropriate.
Monster did not respond to requests for comment from The Washington Post. But he said in an email to customers two days after hackers announced the breach that the company had suffered an “alleged security incident” and asked customers to report back any “unusual account activity.”
“You are in our prayers today,” Monster wrote last week, as news of the hack spread. “When situations arise where individuals might not have honorable intentions, I pray for them. I believe that what the enemy intends for evil, God invariably transforms into good. Blessings to you all.”
Since the hack, Epik’s security protocols have been the target of ridicule among researchers, who’ve marveled at the site’s apparent failure to take basic security precautions, such as routine encryption that could have protected data about its customers from becoming public.
The files include years of website purchase records, internal company emails and customer account credentials revealing who administers some of the biggest far-right websites. The data includes client names, home addresses, email addresses, phone numbers and passwords left in plain, readable text. The hack even exposed the personal records from Anonymize, a privacy service Epik offered to customers wanting to conceal their identity.
Similar failings by other hacked companies have drawn scrutiny from the Federal Trade Commission, which has probed companies such as dating site Ashley Madison for failing to protect their customers’ private data from hackers. FTC investigations have resulted in settlements imposing financial penalties and more rigorous privacy standards.
“Given Epik’s boasts about security, and the scope of its Web hosting, I would think it would be an FTC target, especially if the company was warned but failed to take protective action,” said David Vladeck, a former head of the FTC’s consumer protection bureau, now at Georgetown University Law Center. “I would add that the FTC wouldn’t care about the content — right wing or left wing; the questions would be the possible magnitude and impact of the breach and the representations … the company may have made about security.”
The FTC declined to comment.
Researchers poring through the trove say the most crucial findings concern the identities of people hosting various extremist sites and the key role Epik played in keeping material online that might otherwise have vanished from the Internet — or at least the parts of the Internet that are easily stumbled upon by ordinary users.
“The company played such a major role in keeping far-right terrorist cesspools alive,” said Rita Katz, executive director of SITE Intelligence Group, which studies online extremism. “Without Epik, many extremist communities — from QAnon and white nationalists to accelerationist neo-Nazis — would have had far less oxygen to spread harm, whether that be building toward the Jan. 6 Capitol riots or sowing the misinformation and conspiracy theories chipping away at democracy.”
The breach, first reported by the freelance journalist Steven Monacelli, was made publicly available for download last week alongside a note from Anonymous hackers saying it would help researchers trace the ownership and management of “the worst trash the Internet has to offer.”
After the hackers’ announcement, Epik initially said it was “not aware of any breach.” But in a rambling, three-hour live-stream last week, Monster acknowledged there had been a “hijack of data that should not have been hijacked” and called on people not to use the data for “negative” purposes.
“If you have a negative intent to use that data, it’s not going to work out for you. I’m just telling you,” he said. “If the demon tells you to do it, the demon is not your friend.”
Several domains in the leak are associated with the far-right Proud Boys group, which is known for violent street brawls and involvement in the Jan. 6 attack on the Capitol and was banned by Facebook in 2018 as a hate group.
A Twitter account, @epikfailsnippet, that is posting unverified revelations from the leaked data, included a thread purporting to expose administrators of the Proud Boys sites. One man who was identified by name as administrator of a local Proud Boys forum was said to be an employee of Drexel University. The university said he hasn’t worked at Drexel since November 2020.
Technology news site the Daily Dot reported that Ali Alexander, a conservative political activist who played a key role in spreading false voter fraud claims about the 2020 presidential election, took steps after the Jan. 6 siege to obscure his ownership of more than 100 domains registered to Epik. Nearly half reportedly used variations of the “Stop the Steal” slogan pushed by Alexander and others. Alexander did not reply to requests for comment from the Daily Dot or, on Tuesday, from The Post.
Extremism researchers urge careful fact-checking to protect credibility, but the data remains tantalizing for its potential to unmask extremists in public-facing jobs.
Emma Best, co-founder of Distributed Denial of Secrets, a nonprofit whistleblower group, said some researchers call the Epik hack “the Panama Papers of hate groups,” a comparison to the leak of more than 11 million documents that exposed a rogue offshore finance industry. And, like the Panama Papers, scouring the files is labor intensive, with payoffs that could be months away.
“A lot of research begins with naming names,” Best said. “There’s a lot of optimism and feeling of being overwhelmed, and people knowing they’re in for the long haul with some of this data.”
So hacking and taking down ISIS twitter accounts and Scientology stuff wasn't worth much?Bloody paywall, "democracy dies in the dark" except if that darkness is a paywall, eh? Anyway, surprised to see anonymous do something of political worth for once.
And you only hold it up to one party to do so.And two wrong still will not make a right. You'd think the party / side claiming to be better would want to I dunno try to live up to that ideal a bit more?
I'm done with you. You can't even ATTEMPT to mouth a criticism about the God Emperor or admit he was wrong on anything. You can't even formulate any kind of disagreement.Which at the time was being looked into as a possible treatment (in before people bring up the Brazilian study showing it doesn't work where the Doctors were found to be giving patient 10 times or more the recommended doses). Trump probably got briefed on it by medical advisers and said about it because Trump wanted to try and give people hope or something. Oh and half the controversy around it started because a life long democrat voter claimed she'd given it to her husband and herself because she heard Trump say about it on the news.......... A life long Democrat voter with a social media history of saying how Trump couldn't be trusted and court convictions for domestic violence against partner previously and somehow her husband died of the fish tank cleaner poisoning while she survived well enough that within a week or less she was selling her story to the press........
The last time I talked to someone like you, he sent my blood pressure to the stratosphere and caused physical pain. I'm not letting that happen again. Have a nice life, we won't be talking again.
I don't think you realise but as terrible as it may seem most of the madness still aligns with the purported values of one side. I may not agree with them but at least they're pretty damn consistent in it.And you only hold it up to one party to do so.
What was the saying about Robber Barons being preferable again?
I've criticised Mr Fart in the past (Trump is a slang English term for farting). I'm not going to play the game of trotting out the narratives against him that I know are based on half truths or outright lies. Like it or not in the press conference where he brought said stuff up he even said he'd been told by his medical advisers about it. He wasn't being cryptic and hiding stuff that time he was being open in the hopes the idea of such stuff working could bring hope to people. I'm not going to slap down and act of transparency and attempting to trust the public which it seems didn't actually go horribly wrong.I'm done with you. You can't even ATTEMPT to mouth a criticism about the God Emperor or admit he was wrong on anything. You can't even formulate any kind of disagreement.
The last time I talked to someone like you, he sent my blood pressure to the stratosphere and caused physical pain. I'm not letting that happen again. Have a nice life, we won't be talking again.
I had to do some double takes here... Please tell me he's being sarcastic.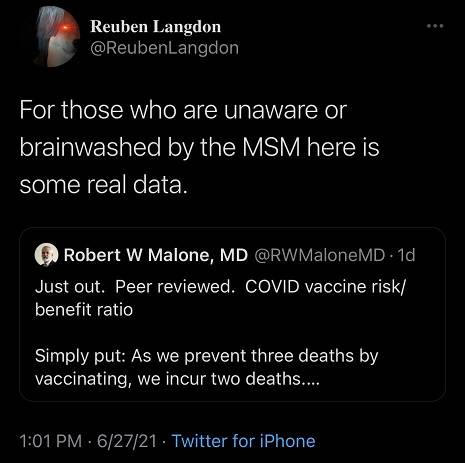
The character you voice is calling you an idiot right now.
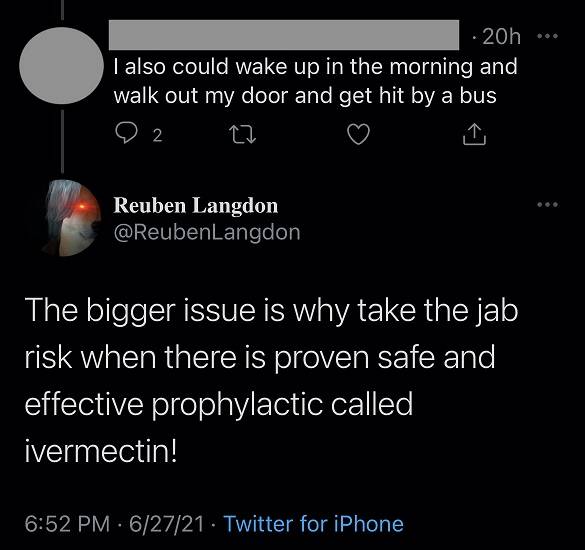
Unfortunately, no. Reuben has been known to spout far right conspiracy theories for years sadly. It's just getting more noticed now. I found out on the DMC forums a couple of years ago, and these images I found on the DMC5 GameFAQS forum.I had to do some double takes here... Please tell me he's being sarcastic.
So much for filling dark souls with LIiiiIGHT.Unfortunately, no. Reuben has been known to spout far right conspiracy theories for years sadly. It's just getting more noticed now. I found out on the DMC forums a couple of years ago, and these images I found on the DMC5 GameFAQS forum.
That was Drew Coombs (Dante's voice in DMC1), but I much appreciate it either way. Reuben did say the line once at a convention back in the mid 2000s.So much for filling dark souls with LIiiiIGHT.
"...wait, even if his math was correct, getting the vaccine is what, 50% better than not" is what I would've said if he didn't go on to say that we should be taking deworming medication preemptively
Welcome to Anti-Woke world where Private companies doing what hey like is now being taken to mean companies in some places are banning people wearing masks

 www.cnn.com
www.cnn.com

A Texas couple wore face masks at a restaurant to protect their immunocompromised infant. The owner asked them to leave | CNN
A Texas couple landed themselves a much needed night out with some friends but it was cut short after the restaurant they were dining at kicked them out for wearing face masks, which they say was in an effort to protect their immunocompromised 4-month-old son.
That's bizarre and stupid.Welcome to Anti-Woke world where Private companies doing what hey like is now being taken to mean companies in some places are banning people wearing masks

A Texas couple wore face masks at a restaurant to protect their immunocompromised infant. The owner asked them to leave | CNN
A Texas couple landed themselves a much needed night out with some friends but it was cut short after the restaurant they were dining at kicked them out for wearing face masks, which they say was in an effort to protect their immunocompromised 4-month-old son.www.cnn.com
But Fauci said once that masks don't work! Doesn't that mean THEY'RE in the wrong?!That's bizarre and stupid.
Sorry for the double post, but what the fuck are conservatives getting all bent out of shape about with that Prince harry Time magazine cover?
